"Waaaay better than MDR"
Master the chaos. Focus on what matters. Secure with confidence.

Integrate Your Tools for
Complete Visibility
Bring the tools you already have and we'll bring you system level visibility and enterprise-grade security operations that deliver clarity in the midst of chaos and the confidence that tools alone cannot provide.



+ More
Users
User authentication events, login anomalies, and access violations.



+ More
Suspicious messages, policy violations, and communication threats.



+ More
Network
Traffic anomalies, connection attempts, and infrastructure events.



+ More
Devices
System changes, process activities, and device health status.



+ More
Apps
Usage violations, configuration changes, and service disruptions.



+ More
Data
Access violations, file changes, and information movement activities.

Billions of daily events triaged between 1~20 seconds
Add Our Enterprise-Grade
Security Operations
We process billions of events daily and respond with incredible speed and accuracy. Our elite people, process, and technology give customers protection otherwise exclusive to much larger organizations.
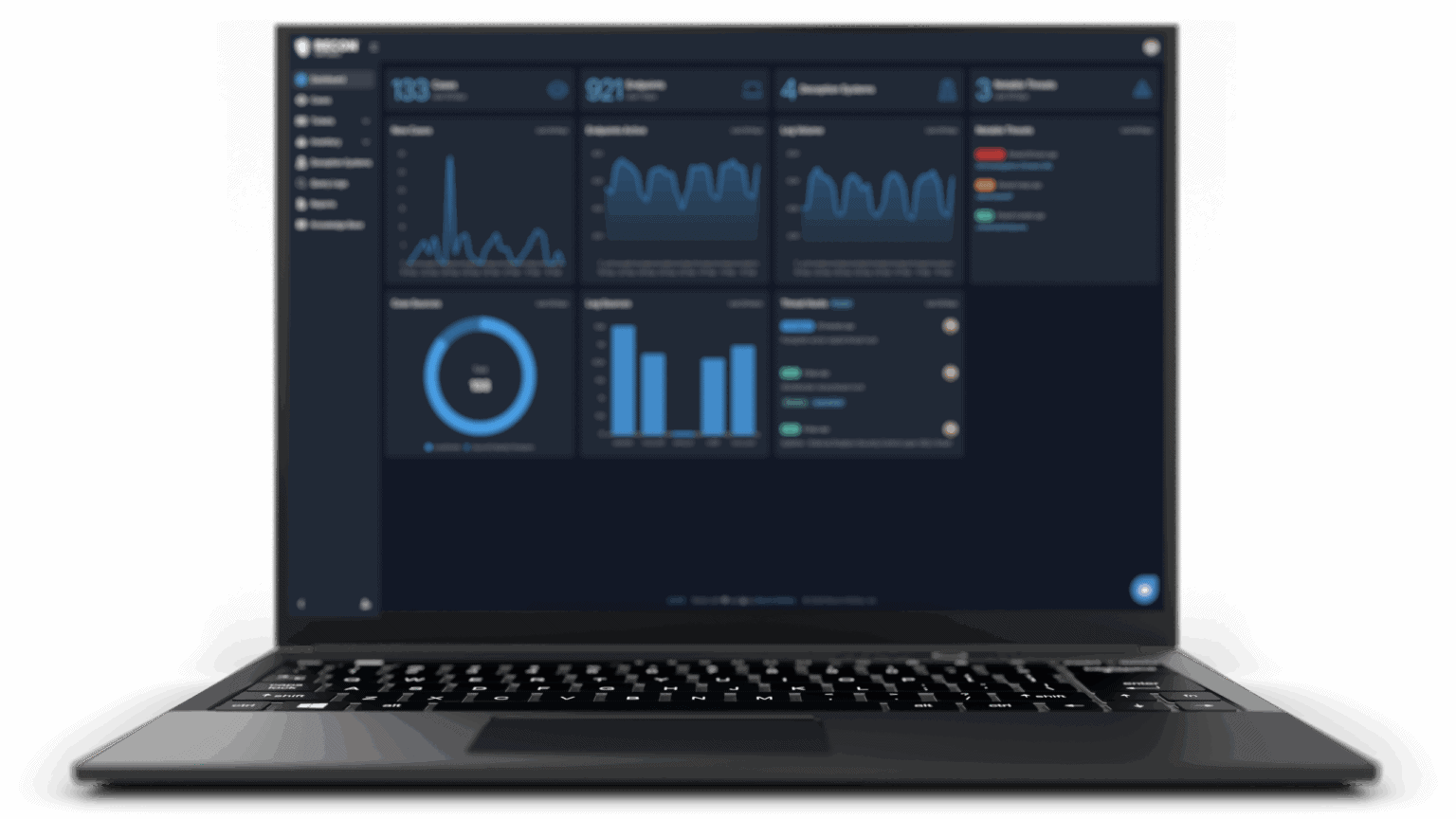
Recon Cybersecurity Platform
Recon's Managed Security Operations use a comprehensive cybersecurity stack with over 6000 proprietary detections and fully managed SIEM and SOAR, delivering system level detections and Fortune 100 protection to mid-sized organizations.

Recon SOC
Recon's SOC is staffed with seasoned professionals each involved with detections, investigations, and response. They conduct proactive threat hunts with an "assumed breach" approach, and the latest intelligence, to shape new detections and help customers stay ahead of emerging threats.

Give Your Team
AI Superpowers
Access the same portal as our SOC, built on our best-in-class platform with pre-built queries, advanced AI capabilities, and consolidated telemetry. View asset inventory, log sources, integrations, and active investigations, plus chat with analysts or ReconAI for unparalleled transparency and capabilities.

Focus on What Matters
Secure with Confidence
The net result of complete visibility and our enterprise-grade security operations is the ability to plan and act in advance, not just react. When a genuine threat does present itself, we'll be there to respond in the manner most appropriate.
Automated Response
Upon incident detection, our automated systems can immediately execute response playbooks tailored to your environment. These systems isolate affected assets and initiate containment procedures, providing rapid response while our experts prepare for investigation.
Best For:
High-volume, routine threats or after-hours incidents requiring immediate containment before human analysis.
Guided Response
When an incident occurs, our security experts can remotely assess the situation and provide technical guidance while your team executes the response. We'll direct containment strategies and support remediation while maintaining your operational control.
Best For:
Organizations with capable internal teams who need expert direction during complex incidents.
Immediate Incident Response
In case of a major incident, our team knows your environment better than anyone else and can respond quickly. They will work to contain the incident and remove the bad actor as well as begin performing a root cause analysis.
Best For:
Critical incidents requiring prompt expert intervention or organizations with limited internal security resources.
Learn why our customers gave us a
97+ Net Promoter Score
2025 Survey